Debian11, Server, RKHunter to check for malwares and corruptions
RKHunter installation and configuration to check for critical files changes against automatic snapshots and for known rootkits. It also checks for processus with open descriptor on deleted files, for binaries which are actually scripts, … This helps to detect when a system was compromised.
- RKHunter presentation
- Prerequisites
- RKHunter installation
- Configuration
- Test
- Materials and links
- Footnotes
RKHunter presentation
rkhunter means Root Kit Hunter. A Root kit is a set of programs installed by crackers when they manage to penetrate a system. It can be installed by viruses also. These programs are meant to send information from the infected system to the cracker’s machines or to execute any arbitrary command on behalf of the infected system owner’s. RKHunter has a database of known root kits and searches for any trace of these rootkits. It also takes fingerprints of critical system programs to detect any change. It automates the snapshots with apt at each package installation. It sends email notifications to the administrators when something was detected. I use RKHunter for the root kit database, I’ll install another tool, tripwire for the critical files alteration detection in the next post.
Prerequisites
This article only depends on the Generic machine preparation post serie.
RKHunter installation
I first give to debconf the answers to the questions which will be asked by the package at installation. I want RKHunter to be executed every day to check my filesystem, I want it to update the vulnerabilities database automatically and I want it to be automatically executed after each package installation to take a fingerprint of the supposed-clean package files. This last one can be dangerous if you use apt to install, upgrade or remove a package, it will automatically trigger a new snapshot and will legitimate current files. This is my choice for my architecture and I know what I’m doing on my servers, be sure to understand before applying.
echo 'rkhunter rkhunter/cron_daily_run boolean true' | debconf-set-selections
echo 'rkhunter rkhunter/cron_db_update boolean true' | debconf-set-selections
echo 'rkhunter rkhunter/apt_autogen boolean true' | debconf-set-selections
apt-get install -y rkhunter
Configuration
Configure email notifications
RKHunter will send email notifications when something goes wrong during either a filesystem check or a vulnerability database update. Thus, I need to configure the email address and email command to send emails. Whatever happen, it also sends the details by email in another message.
sed -i 's/#\?MAIL-ON-WARNING=.*/#MAIL-ON-WARNING=root@localhost/' /etc/rkhunter.conf
sed -i 's/#\?MAIL_CMD=.*"/MAIL_CMD=mail -s "[rkhunter] Warnings found for \${HOST_NAME}"/' /etc/rkhunter.conf
Configure database update
RKHunter needs to update its known vulnerability database from time to time. I configure the download tool to use, the email notifications and I enable this automatic updates.
sed -i 's/#\?WEB_CMD=.*/WEB_CMD=wget/' /etc/rkhunter.conf
sed -i 's/DB_UPDATE_EMAIL=".*"/DB_UPDATE_EMAIL="true"/' /etc/default/rkhunter
sed -i 's/#\?UPDATE_MIRRORS=.*/UPDATE_MIRRORS=1/' /etc/rkhunter.conf
sed -i 's/#\?MIRRORS_MODE=.*/MIRRORS_MODE=0/' /etc/rkhunter.conf
Ignore known false positives
After bedtesting in a closed environment, I listed all the alerts relative to a normal activity and adjusted the configuration to tell RKHunter that these alerts are normal and should not trigger warnings. The last one is because I do accept direct root connections with a key. You might not.
echo 'ALLOWPROCDELFILE=/usr/sbin/cron' >> /etc/rkhunter.conf
echo 'ALLOWPROCDELFILE=/usr/bin/dash' >> /etc/rkhunter.conf
echo 'ALLOWPROCDELFILE=/usr/bin/run-parts' >> /etc/rkhunter.conf
echo 'SCRIPTWHITELIST=/usr/bin/egrep' >> /etc/rkhunter.conf
echo 'SCRIPTWHITELIST=/usr/bin/fgrep' >> /etc/rkhunter.conf
echo 'SCRIPTWHITELIST=/usr/bin/which' >> /etc/rkhunter.conf
echo 'PORT_PATH_WHITELIST=/usr/sbin/portsentry' >> /etc/rkhunter.conf
echo 'ALLOW_SSH_ROOT_USER=prohibit-password' >> /etc/rkhunter.conf
Miscellaneous configuration
I also uncomment the dhclient line, because it was relevant in some cases, but you can keep it commented if you dont use dhclient. I activate the whole test suite and activate the SSH protocol version check, v1 should not be allowed, it is disabled and should remain disabled !
sed -i 's~#\?ALLOWPROCLISTEN=/sbin/dhclient~ALLOWPROCLISTEN=/sbin/dhclient~' /etc/rkhunter.conf
sed -i 's/^DISABLE_TESTS/#&/' /etc/rkhunter.conf
sed -i 's/^#\?PKGMGR=.*/PKGMGR=DPKG/' /etc/rkhunter.conf
sed -i 's/^#\?\(ALLOW_SSH_PROT_V1\)=.*/\1=0/' /etc/rkhunter.conf
Open IPTables for updates
RKHunter needs to update its vulnerabilities database. We configured an automatic update and it needs to download files from Internet but the IPTables firewall blocks outgoing traffic by default, if not explicitely allowed. Thus, we need to create a new chain to list the RKHunter repositories IP addresses and to include this chain in the WAN_output validation chain :
sed -i 's/^-N WAN_input$/-N RKHunterRepositories\n-A RKHunterRepositories -d 216.105.38.10 -j ACCEPT\n\n&/' /etc/iptables/rules.v4
sed -i 's/^-N WAN_output$/&\n-A WAN_output -p tcp --dport 80 --tcp-flags FIN,SYN,RST,ACK SYN -j RKHunterRepositories/' /etc/iptables/rules.v4
systemctl restart netfilter-persistent
Update the malware database
Now, we can initiate the first database update manually to check the firewall rules and be sure that automatic updates will succeed.
rkhunter --update
Initial snapshot of system files
It is time to take a snapshot of the sytem files. RKHunter will compute hashes for critical files in the system and store the hashes. It is configured to execute this snapshot after each package upgrade, install or removal in the apt suite, to keep the hashes database up-to-date. Then, the file alteration check is configured to be executed everyday. Anyway, I’ll also install tripwire for this specific task, in the next post of this blog serie.
rkhunter --propupd
Test
Test check
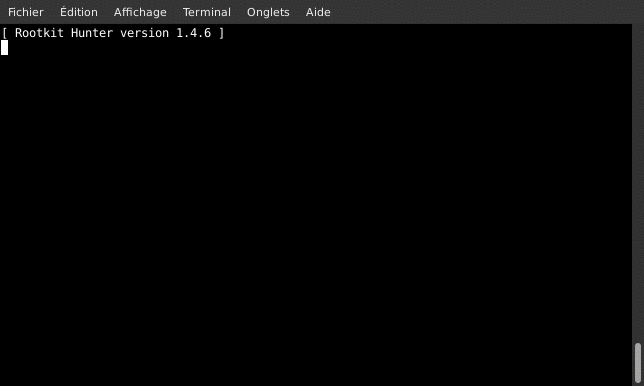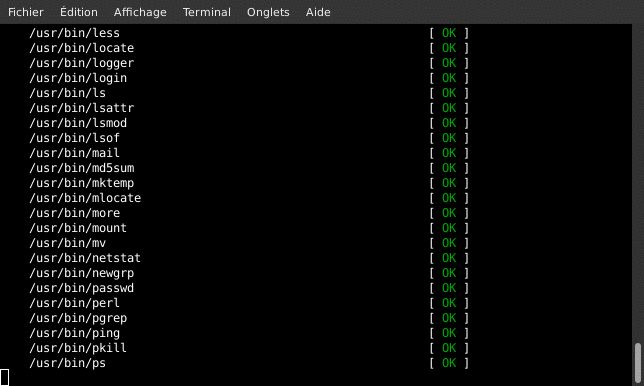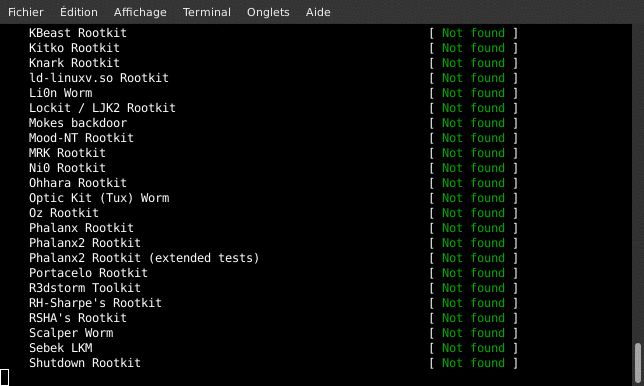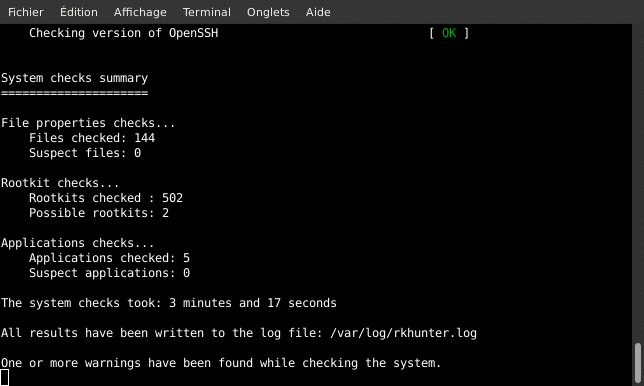
Let’s execute a full test, with realtime colored output !
rkhunter -c --enable all --disable none --skip-keypress
Email test
Let’s execute a faster test, with email notification to check that the notifications are also working.
/etc/cron.daily/rkhunter